Antivirus Evasion
security hacking av amsi defender bypassEstimated reading time: 4 minutes
A lot of organizations and companies run antivirus software on their users clients. Users should be protected from themselves by preventing the execution of .exe files or scripts. Through GPOs and standard tools of the OS, this can be achieved. In this post we’ll be mainly talking about how to bypass tools like AMSI1 and Windows Defender.
Antivirus Software
The first AV software originated back in 1972. Since the first known Virus was the so called “Creeper Virus”2, Ray Tomlinson used to write the “Reaper”3, a program to remove it. AV software today is not only used to detect and remove viruses, but other type of malware like trojans, rootkits, backdoors and currently popular encryption-based ransomware.
AV software uses different types of mechanism to detect viruses. The traditional method is so called signature-based detection4. To do this, every AV software has a databases which contains signatures of known viruses, and compares both of them. If the signatures match, the binary get’s flagged as malicious.
Bypassing Signature Detection
The most popular approach for obfuscation in the past was to modify the code of binaries and scripts by renaming keywords which are known to trigger AVs. An example would be to rename mimikatz5 to mimidog. This worked for a short while but is not worthwhile anymore.
Trying to obfuscate the mimikatz binary results in not only changing variable names, but also filenames of dll’s, configuration files and shorten a lot of code.
When it comes down to obfuscating these, there are some ways to do so:
- Encrypt text/files/scripts
- Rename functions and variables
- Remove Comments
- Write own code
By doing this, we have a chance of bypassing AV software for the most part. However, AMSI and Windows Defender are doing a good job nowadays in detecting popular scripts like the ones from PowerSpoit6.
AMSI
What is AMSI?
Straight up from Microsoft:
“The Windows Antimalware Scan Interface (AMSI) is a versatile interface standard that allows your applications and services to integrate with any antimalware product that’s present on a machine. AMSI provides enhanced malware protection for your end-users and their data, applications, and workloads.1”
So basically AMSI is an API for applications/services (like Windows Defender), this includes of course PowerShell too.
Downgrading PS
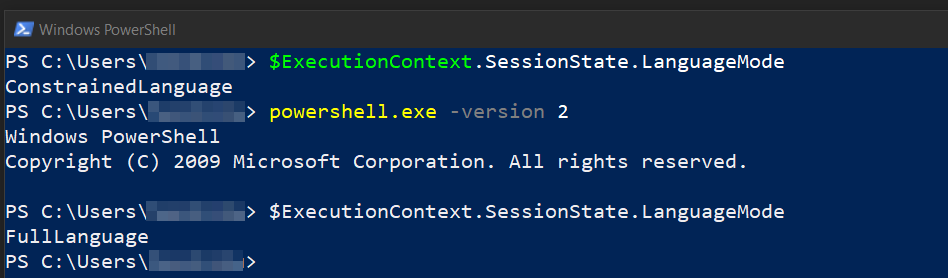
The first and easiest way to bypass AMSI and also Constrained Language Mode7 is by downgrading PS to an older version (mainly v2)
PS> powershell -version 2
Although PS v2 is deprecated (by Microsoft), it’s still present in the OS. We use version 2 of PS, because it doesn’t contain security features like AMSI.
A normal user can enable this feature under “Turn Windows features on or off”
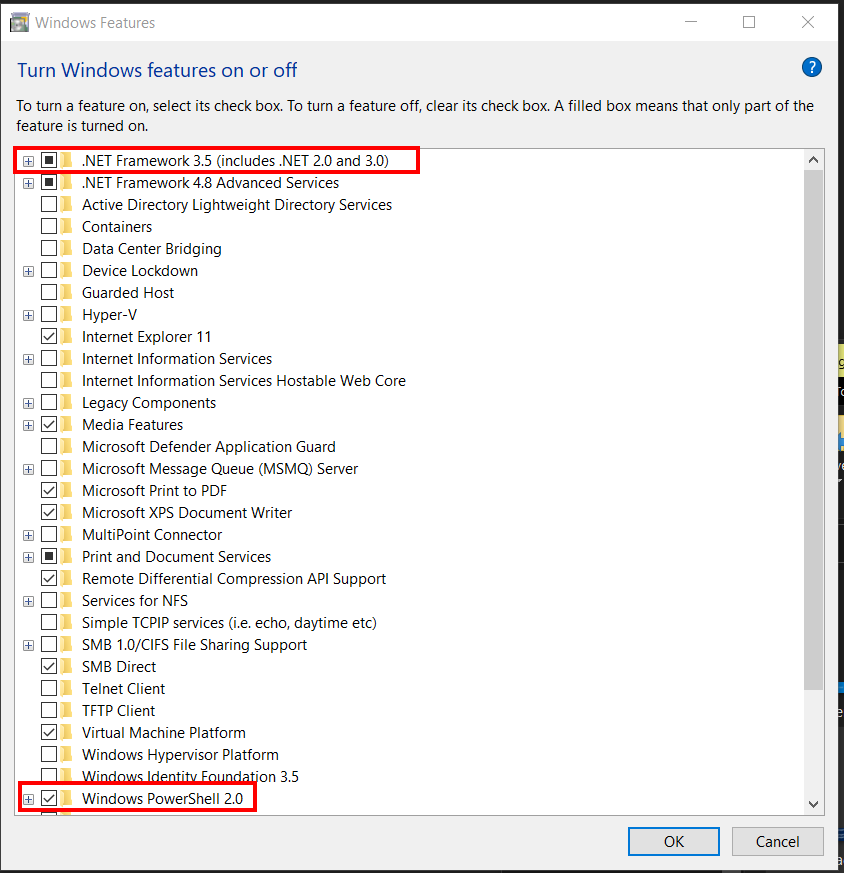
Then we start PS in version 2 and see that we are in “FullLanguage” instead of “ConstrainedLanguage”.
AMSI Fail
Another method to bypass AMSI is to use AMSI fail8.
Quote straight from their website:
“AMSI.fail generates obfuscated PowerShell snippets that break or disable AMSI for the current process. The snippets are randomly selected from a small pool of techniques/variations before being obfuscated. Every snippet is obfuscated at runtime/request so that no generated output share the same signatures.”
There are other methods like memory patching, base64 encoding and DLL hijacking. A good read on how to perform these AMSI bypasses can be found here: https://pentestlaboratories.com/2021/05/17/amsi-bypass-methods/
Renaming Keywords
The practical way we want to show to bypass AMSI (and Defender), is to rename keywords and functions of the scripts we want to use. Instead of saving our PS code as a file, which would touch the disk, we will use PowerShell ISE to execute the code directly from memory. It’s also more convenient to modify the PS code inside ISE itself.
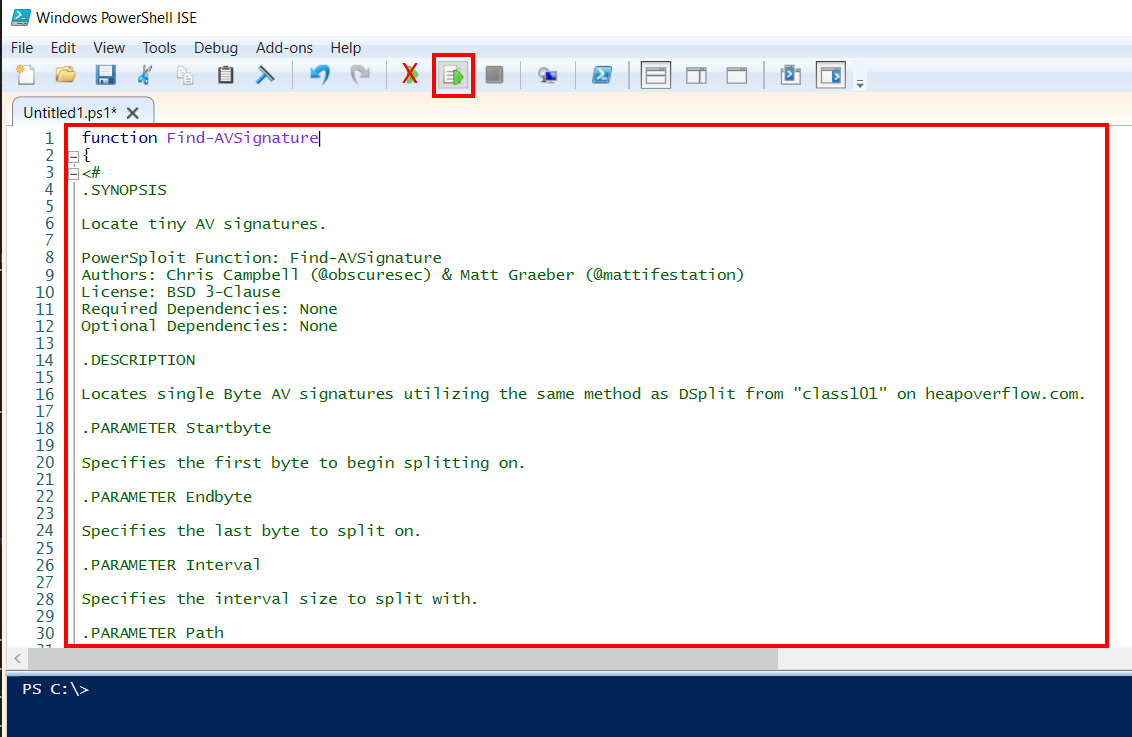
To execute our pasted script we need to select the whole text (CTRL+A) and press F8 (ISE executes the selected script). If we press the green playbutton ISE will the script localy which touches the disk.
For this example we used Powersploits Find-AVSignature module which we loaded raw into PS ISE and renamed it to Find-Kitty.
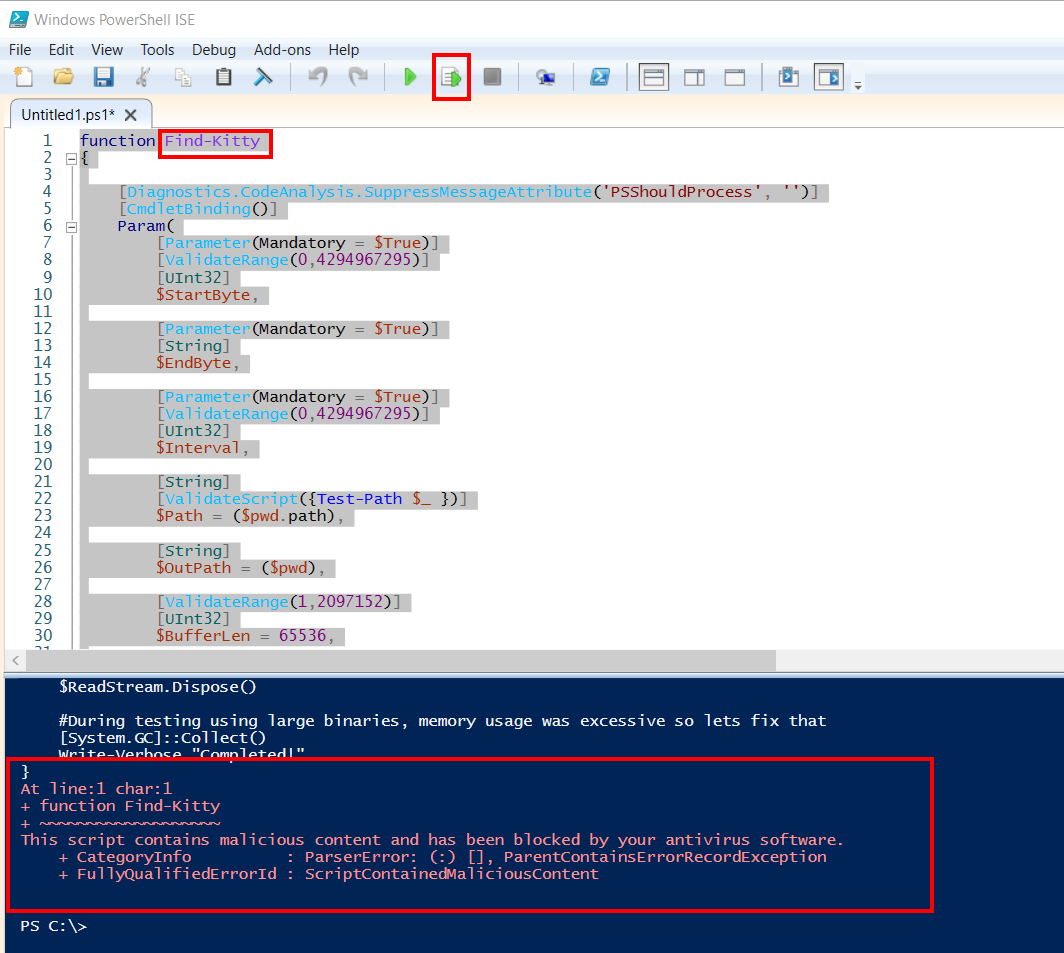
If renaming the function also results in an error, we can go one step further and start to rename variable names.
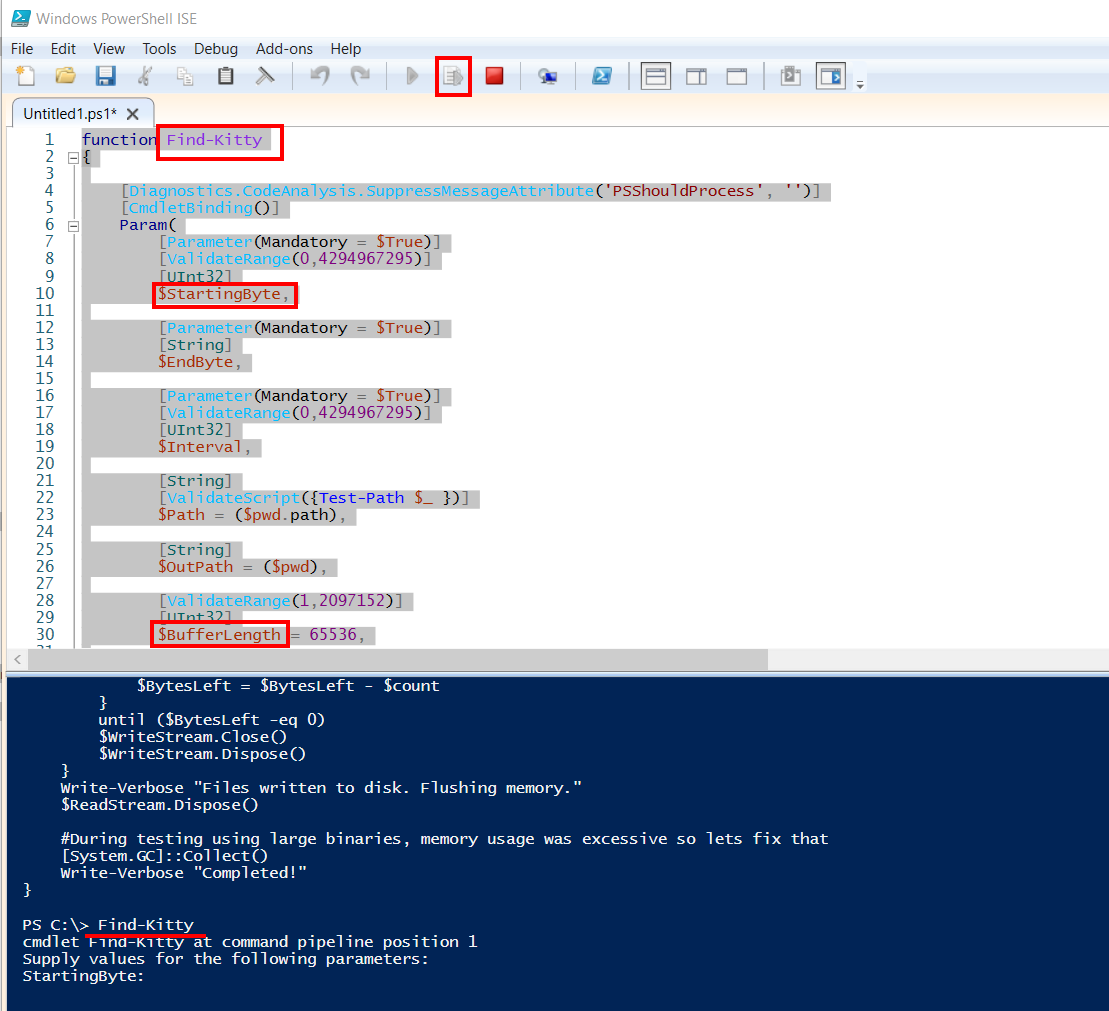
With our variables $StartByte and $BuffLen renamed, we can execute the script and it is no longer flagged by Windows Defender.
We see that renaming a few keywords helps us bypassing AMSI (and Defenders real-time protection). This technique can also be used for reverse shells like nishang9.