xz
backdoor security xz utils tools oss softwareEstimated reading time: 1 minutes
For various reasons I wasn’t able to write a summary for 2023. But if I had known then what to expect in 2024 with the current xz/liblzma1, I would have written a modified version of Wilhelm Hey’s “Alle Jahre wieder”2 instead of the recap.
As for the vulnerability itself, there are already a number of blogs on the subject, the best known being by Evan Boehs3 and Bruce Schneier4.
My two cents? Yes, open source, like any software, can be backdoored (and abused). The good news? Unlike closed-source software, such backdoors can be found and fixed quickly. The bad news? Many projects, even those widely used in industry, are managed by individual developers, usually without compensation.
As always, a picture is worth a thousand words:
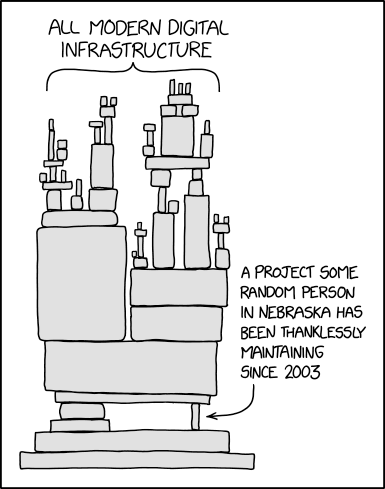
Let’s update that a litte bit:
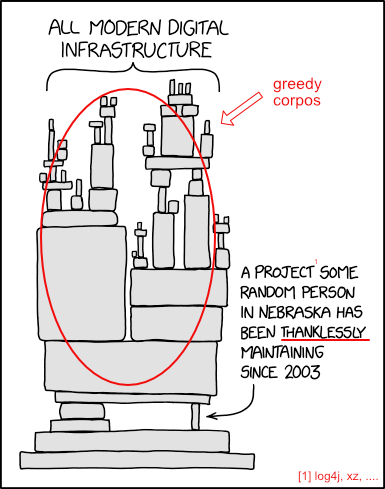
And finally, to all free software developers: DO NOT let others (especially large corporations) demand things from you, in particular if they take your work for granted without paying for it!