Passwords
security hacking passwordsEstimated reading time: 2 minutes
It’s rather bad than complex
A lot of users1 always choose their passwords based on the same criteria:
-
They use the same password for every service
password reuse -
They use a combination of username + year of birth
user95 -
The classic par excellence: season + year
Winter2020
With common password lists, these kind of passwords can be found out in seconds. Even if they’re hashed, cracking them with tools like Hashcat2 in combination with rule based lists3 and potent hardware is not a big effort.
Convenience plays a big role, but also the fact that some password generators produce output like A8(;o![x3nMLh9. Nobody wants to remember something like that, let alone write it down and type it out.
Complexity in detail
But this is also where the dilemma arises. Password policies of websites specify complexity and minimum lengths.
Typical requriments are:
- at least 8 characters
- at least 1 number
- at least 1 special character
- upper and lower case letters
A password like Password123! meets these requirements exactly, but is available in every common word list and thus can be guessed without much effort. Also, the hash of this password 42f749ade7f9e195bf475f37a44cafcb is quickly cracked using so-called Rainbowtables4.
The key is lenght
Let’s do some math: A password consisting of 5 randomly chosen words from a vocabulary of about 3000 words has 3000^5 ≈ 2.34E^17 ≈ 10^17 possible combinations. A password with a length of 9 characters and high complexity (*!?}{,:"';()[]-_ comes to 9^17 ≈ 1.67E16 ≈ 10^16 possible passwords and is approximately equally strong. If you increase the password length to 6 words (3000^6 ≈ 7,29E20 ≈ 10^20), the number of combinations here is comparable to a password of 11 characters (11^20 ≈ 6,72E20 ≈ 10^20).
Therefore I would suggest to use passphrases instead of simple passwords!
A phrase like I drink wine on an ants back is easier to remember than A8(;o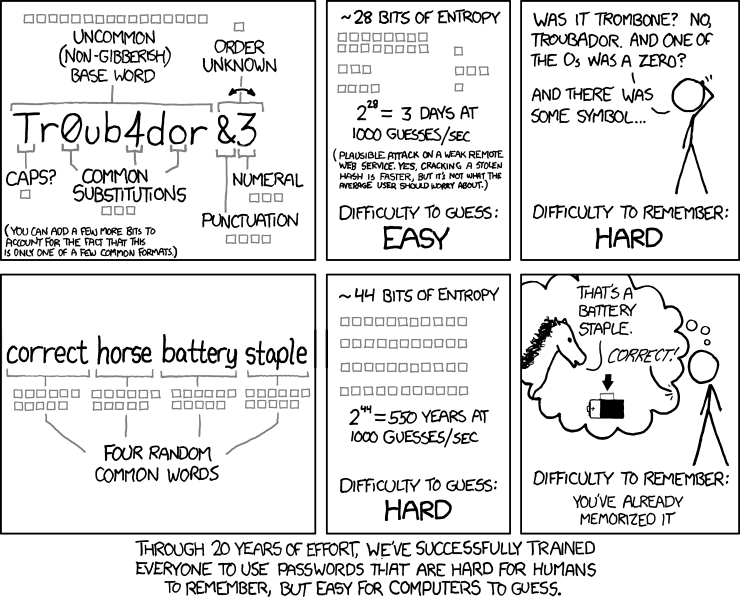
Password manager
Last but not least, something that can help the whole issue a bit: password managers. They allow to store passwords for each account encrypted with a master password or keyfile. Furthermore, most password managers have built-in password generators where password policies can be set. Thus complex passwords like A8(;o![x3nMLh9 as well as passphrases like eating mouse wretched water preach can be generated.